MEGA: Secure Cloud Storage & File Sharing
Is the cloud truly the safest place for our digital lives?MEGA, the encrypted cloud storage provider, makes a compelling case for its security-focused approach.But is it enough to navigate the complex landscape of online threats and privacy concerns?
In a world increasingly reliant on digital data, the question of secure storage becomes paramount. MEGA positions itself as a privacy-centric solution, offering end-to-end encryption that promises to keep user data safe from prying eyes, even their own. This means that files are encrypted and decrypted on the users device, with MEGA holding no decryption keys. This architectural choice differentiates MEGA from other cloud storage providers who can technically access user data. The allure of this approach is clear: true data ownership and control, a safeguard against data breaches, government requests, and even potential vulnerabilities within MEGA itself.
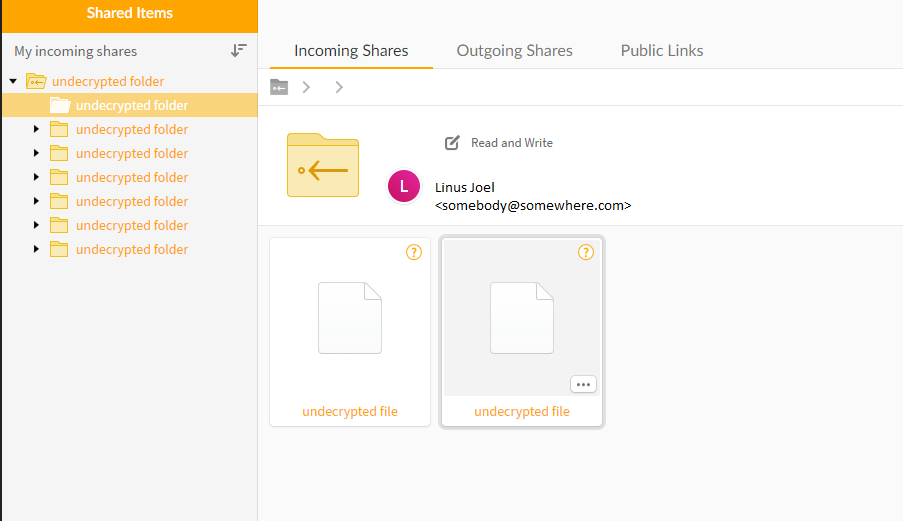
[wp_table id=123]The practical implications of MEGAs security measures are significant. Users can share files and folders of any size with a link, ensuring that only those with the link can access the content, even if they don't have a MEGA account. This granular control extends to syncing functionalities, allowing users to collaborate on shared folders seamlessly across multiple devices. Changes made on one device are automatically reflected on all synced devices and within the MEGA cloud, facilitating real-time collaboration while maintaining the integrity of the encryption.
Beyond individual users, MEGA also offers solutions for developers. The "megacmd" command-line tool provides access to all MEGA account functionalities, allowing for automated backups, scripting, and integration with other systems. This expands the potential of MEGA beyond simple file storage, offering a versatile platform for developers to build upon.
However, this robust security model isn't without its nuances. The very nature of end-to-end encryption means that lost passwords translate to lost data. MEGA cannot retrieve lost keys, placing the responsibility of key management squarely on the user. While this reinforces the principle of user control, it also introduces a potential point of failure. Users must diligently safeguard their passwords, understanding that losing them means irrevocably losing access to their data.
Another aspect to consider is the potential for malicious actors to leverage MEGAs encryption for illicit purposes. While MEGA itself cannot access user data, the platform could unknowingly host illegal content, posing challenges for law enforcement and raising ethical considerations.
Despite these complexities, MEGA's commitment to user privacy and data security is undeniable. The platform offers a robust suite of features, from file sharing and syncing to developer tools, all underpinned by end-to-end encryption. In a world where data breaches are increasingly common, MEGA's approach offers a compelling alternative, shifting the power dynamic back to the user. The onus, however, remains on the user to understand the implications of this power and act accordingly, safeguarding their keys with the same diligence that MEGA applies to protecting their data.
MEGA's approach is not merely about storing files; its about owning them. Its a philosophy that resonates with growing concerns about data privacy in the digital age, offering a haven for those seeking true control over their digital lives.
Furthermore, the ability to share files securely, even with those who don't have a MEGA account, simplifies collaboration while preserving privacy. The seamless syncing across devices adds another layer of convenience, making MEGA a practical solution for everyday use.
For developers, the "megacmd" tool unlocks a world of possibilities, transforming MEGA from a simple storage solution into a powerful platform for building secure applications and automating workflows.
The challenge for MEGA, moving forward, will be to balance its unwavering commitment to security with the evolving needs of users and the broader online ecosystem. This includes educating users about the importance of key management and addressing the potential misuse of the platform while maintaining its core principle of user privacy.

Detail Author:
- Name : Miss Mayra Kovacek
- Username : mcclure.bulah
- Email : sdamore@yahoo.com
- Birthdate : 2001-02-18
- Address : 89019 Bahringer Via New Marvin, TX 69870
- Phone : +1 (586) 672-1273
- Company : Eichmann Ltd
- Job : Taxi Drivers and Chauffeur
- Bio : Cupiditate architecto ad praesentium sint. Atque iste et soluta repellendus cum. Rerum adipisci consequuntur quis ut est consequuntur.
Socials
instagram:
- url : https://instagram.com/bernier1974
- username : bernier1974
- bio : Est repudiandae fugit quasi modi natus. Aut adipisci accusamus aliquam ea.
- followers : 2982
- following : 1511
linkedin:
- url : https://linkedin.com/in/vaughn.bernier
- username : vaughn.bernier
- bio : Qui debitis eos iure ut quasi voluptatem.
- followers : 5366
- following : 703
twitter:
- url : https://twitter.com/vaughn_bernier
- username : vaughn_bernier
- bio : Ipsa corrupti voluptate architecto non suscipit eum. Est voluptas itaque error iusto. Distinctio aut officia non similique officiis ut.
- followers : 4573
- following : 2450
facebook:
- url : https://facebook.com/vaughnbernier
- username : vaughnbernier
- bio : Sint porro rerum tempora dolor earum id quia quas.
- followers : 2653
- following : 556